Introduction
Lately has been growing in popularity those DDoS attacks based on DNS Amplification, specifically due to the attack to Spamhaus. While this kind of attack is becoming more and more popular at DDoS scenarios there are others types of DDoS techniques being used not so common and which should be known before being hitted by them. In this post i want to introduce amplification attacks using Quake 3 network protocol - UDP based - as well as how to analyze it in several ways to really understand it in depth to find a pattern and create a fingerprint for trying mitigating them.
How does this attack works
This kind of DDoS is very similar to a DNS Amplification Attack, an attacker send thousands of UDP datagrams pretending to be a legitimate Quake 3 client asking for game status with source IP address spoofed using the one wanted to be flooded, then, queried Quake 3 servers will answer with game status - including some server configuration options and user list - to spoofed source IP address, flooding it with thousands of unsolicited UDP datagrams.
I have done a basic draw for illustrating it:
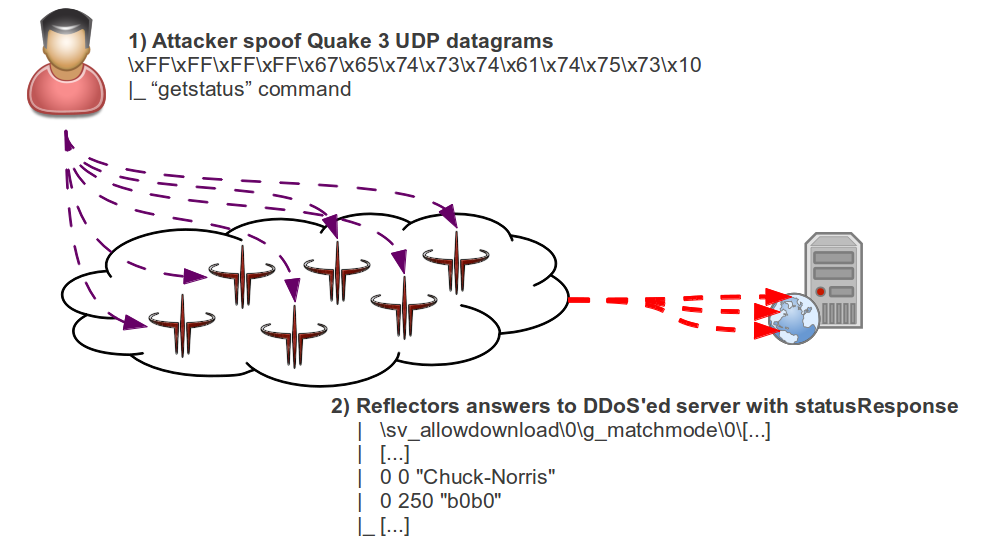
As shown, amplifiers servers - Quake 3 ones - will flood victim with an aggregated throughput much higher than the used by attacker (hence it “amplifier” term); lets see some traffic generated if we make this “getstatus” request:
1 2 3 4 5 6 7 8 9 10 | |
If we calculate amplification ratio we find that sending an UDP datagram of 56 bytes will trigger a response of 1373 bytes, achieving about x24,5 amplification ratio, not bad after all.
Installing Quake 3 server (amplifier)
We are going to need a Quake 3 server for being used as “amplifier” to attack our victim when doing some local tests, so we are going to need an original copy of Quake 3 and compiling ioquake3, an open source Quake 3 engine based on id Software source code (publicly released in 2005).
1 2 3 4 | |
Now we need to copy Quake 3 original pak files (those with models and textures) from our cdrom to our hdd prior being able to run an ioq3 server:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 | |
Our ioq3 server is ready to make some frags!, we can check it with quake3-info.nse script:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 | |
Analyzing attackers script
Commonly used scripts for this kind of attacks has been leaked repeatedly so i’m not going to hide it (regardless of the fact those who DDoS already have it or more powerful attack vectors), so here is a C Quake 3 amplification flooder made upon a generic UDP flooder.
It’s interesting the way UDP datagrams are assembled, so let’s go to analyze it (thanks to NighterMan for helping me with my rusted C knowledge), i have made some comments below about found mistakes, particularly at networking knowledge (the tool doesn’t even work rigth to trigger amplified response):
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 | |
There isn’t much more to say about this, just highlight the fact that using htonl() instead of htons() avoid us using fixed IP ID value when finding an attack pattern. Also found interesting the specified IP ToS value to mess around with congestion detection and avoidance mechanisms, but contrasts with some mistakes that make easier to spot attacking datagrams generated by this tool and, even more unvelievable, incorrect UDP length transform amplification attack just in a plain UDP spoofed attack (probably made some copy paste from here and there), seems some guys need to read a bit about network protocols before playing with DDoS tools…
Crafting Quake 3 amplification attack packet with Scapy
Probably the quick and easiest way to craft packets when doing network tests is Scapy, a python tool to create and manipulate network packets that can be used within his own interactive shell or just as a python package.
Below is an example for crafting this kind of attack with scapy, without spoofing IP address (we want to check answer) and with a correct UDP length value and checksum (scapy will automagically compute values like length and checksum prior of sending any packet):
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 | |
If you have never used scapy before take a look to this scapy-guide made by Adam Maxwell, it’s really useful as a first-steps guide.
How does it looks like at network level?
Ok, so we have readed flooder code and referenced rfc sections (because we did, right? ;) ), time to sniff some attack traffic and analyze it with tshark/wireshark and observe described behaviour pattern.
First, i have compiled and used “dns.c” flooder without making any kind of modification, this is a Wireshak screenshot while analyzing it:
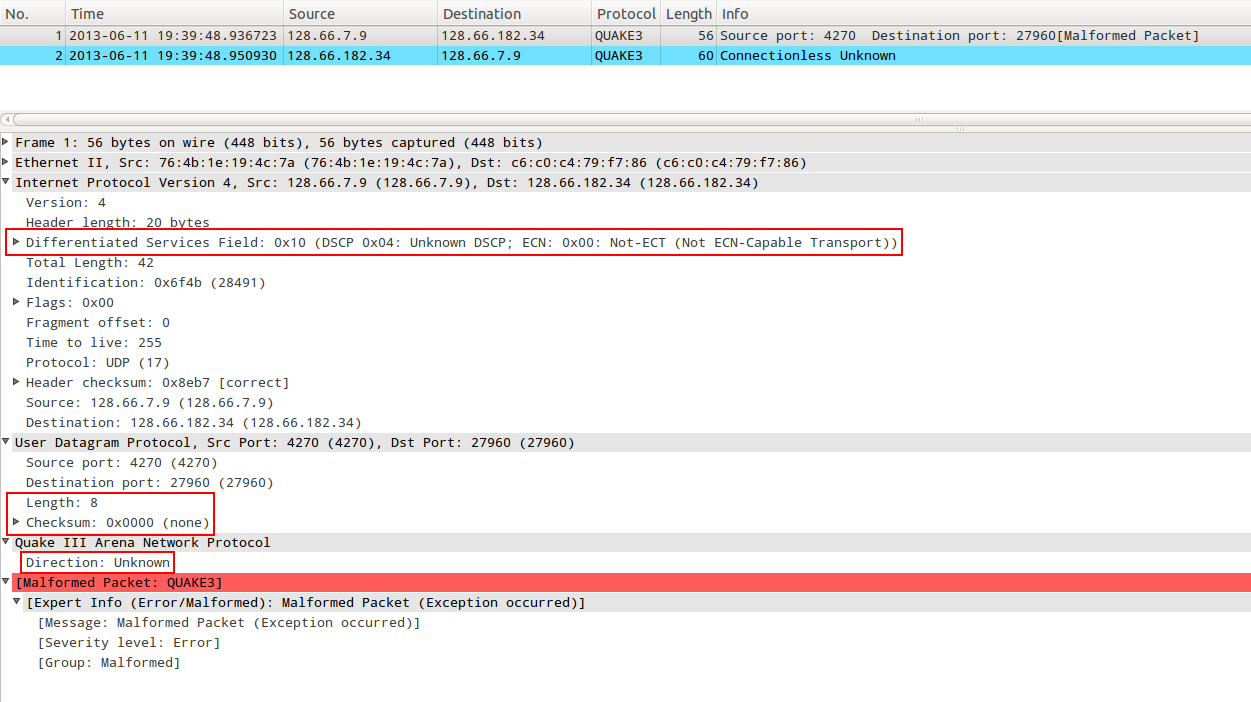
I have marked in red important aspects like ToS/DS field, UDP length/checksum and “direction” (for Quake 3 protocol). As shown, Wireshark Quake 3 protocol dissector itself detect it as a malformed packet, due to UDP length = 8 application layer will receive an empty payload, fact that the Q3 server will treat as a client with connectivity errors and will send a “disconnect” message:
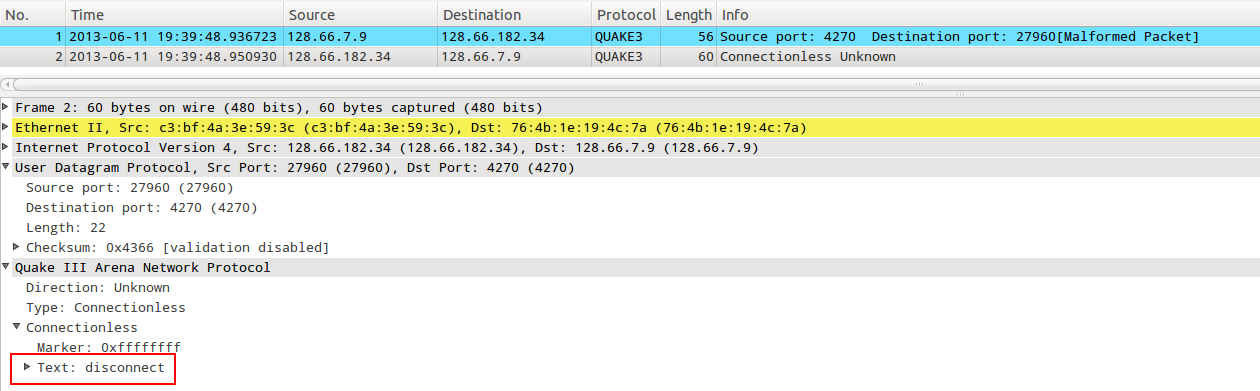
If we compare question size against response answer there is no amplification factor at all, this program would be useful only for provoking Q3 servers sending unsolicited traffic to a third host - the attacked one - with the intention of splitting originating AS-path attacking or something similar.
I have sent one “getstatus” request forged with scapy to a public Quake 3 server (for obvious reasons i have changed some response content):
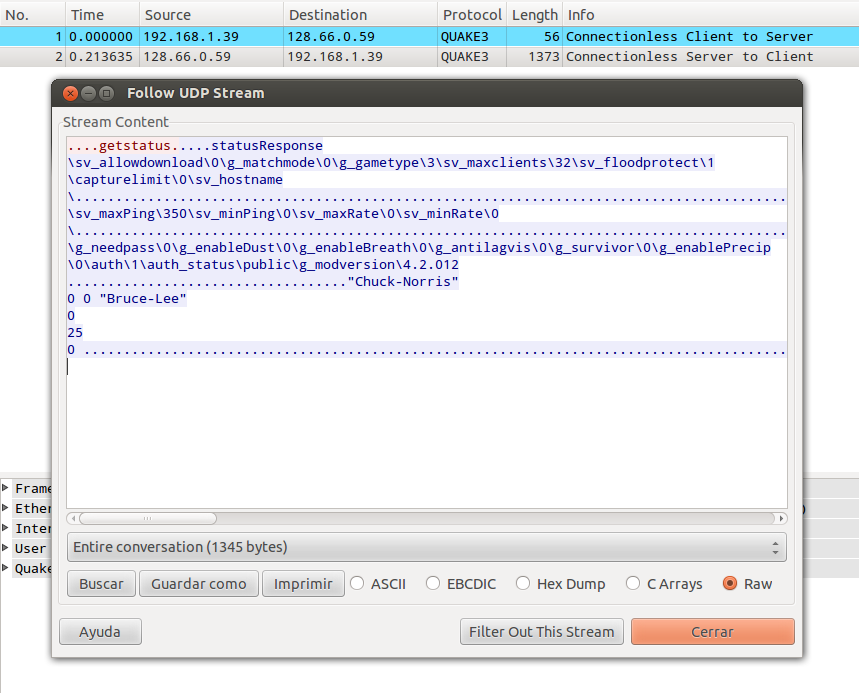
The server now correctly decode UDP payload, process “getstatus” command and answer with server status, including several server options and config values as well as statistics (a response size of 1373 bytes for a 56 bytes request).
Next steps
So far we have seen how this attack works as well as (bad coded) programs being used in the wild to launch DDoS attacks from web panels (the so called DDoS booters). We have also seen how to replay the amplification attack with Scapy and analized a bit of this network traffic with Wireshark.
At the next post we are going to see how to mitigate this kind of attack at the Quake 3 server - at application and network layer - side and also from the victim side being flooded. Also we are going to analyze it deeper with tshark to see potential ways to spot this attack and try to block it.
See you at next post!